- by: Will Sweatman
There’s pandemonium on the streets. You look down from your 4
story apartment and see hundreds of people marching and chanting. You
pick up your phone and call your buddy, expecting it to link up to the
nearest cell tower which will route your call to where it needs to go.
Instead, without your knowledge, you link to a tricked-out police surveillance truck a few blocks away. They intercept your call and listen to the conversation in hopes of tracking the protest.
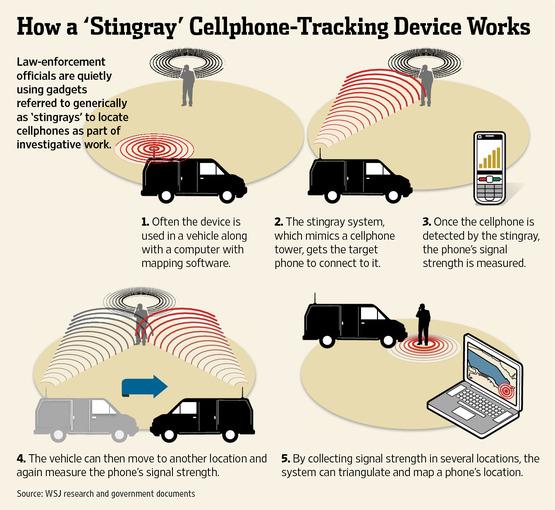 This
scenario undoubtedly took place on November 28th of this year in
downtown Chicago. People began to notice the truck following the
protest, some even complaining that their cell phone stopped working
when it was close by. Most probably had no idea that the police truck
was equipped with Stingray technology. It forces your cell phone to connect to it
as opposed to the nearest cell tower, allowing authorities to listen in
on your conversations and track individual phones by moving and
measuring the difference in signal strength. The hacking group Anonymous
released some audio of a conversation between two officers and a
command center (block-quoted above) which provides damning evidence that
such actions indeed took place on Chicago streets.
This
scenario undoubtedly took place on November 28th of this year in
downtown Chicago. People began to notice the truck following the
protest, some even complaining that their cell phone stopped working
when it was close by. Most probably had no idea that the police truck
was equipped with Stingray technology. It forces your cell phone to connect to it
as opposed to the nearest cell tower, allowing authorities to listen in
on your conversations and track individual phones by moving and
measuring the difference in signal strength. The hacking group Anonymous
released some audio of a conversation between two officers and a
command center (block-quoted above) which provides damning evidence that
such actions indeed took place on Chicago streets.
So here’s the question: Can it be fooled? Can you spoof the spoofer? Can you tell the difference between a signal from a Stingray versus a cell tower? If this is not possible, surely the cell network providers can add something to the signal allowing end users to verify that it is a legitimate signal from a cell tower. But can it be done in a way that a Stingray can’t replicate?
Thanks to [John Tirelli] for the tip!
Dispatch: “CPIC [Chicago police’s spy ‘fusion’ center] on the air for a mobile”
Officer 1: “Go ahead”
Officer 2: “Yeah one of the girls, an organizer here, she’s been on her phone a lot. You guys picking up any information, uh, where they’re going, possibly?”
Officer 1: “Yeah we’ll keep an eye on it, we’ll let you know if we hear anything.”
Officer 2: “10-4. They’re compliant, and they’re, they’re doing ok now but she’s spending a lot of time on the phone.”
Officer 1: “10-4”
 This
scenario undoubtedly took place on November 28th of this year in
downtown Chicago. People began to notice the truck following the
protest, some even complaining that their cell phone stopped working
when it was close by. Most probably had no idea that the police truck
was equipped with Stingray technology. It forces your cell phone to connect to it
as opposed to the nearest cell tower, allowing authorities to listen in
on your conversations and track individual phones by moving and
measuring the difference in signal strength. The hacking group Anonymous
released some audio of a conversation between two officers and a
command center (block-quoted above) which provides damning evidence that
such actions indeed took place on Chicago streets.
This
scenario undoubtedly took place on November 28th of this year in
downtown Chicago. People began to notice the truck following the
protest, some even complaining that their cell phone stopped working
when it was close by. Most probably had no idea that the police truck
was equipped with Stingray technology. It forces your cell phone to connect to it
as opposed to the nearest cell tower, allowing authorities to listen in
on your conversations and track individual phones by moving and
measuring the difference in signal strength. The hacking group Anonymous
released some audio of a conversation between two officers and a
command center (block-quoted above) which provides damning evidence that
such actions indeed took place on Chicago streets.So here’s the question: Can it be fooled? Can you spoof the spoofer? Can you tell the difference between a signal from a Stingray versus a cell tower? If this is not possible, surely the cell network providers can add something to the signal allowing end users to verify that it is a legitimate signal from a cell tower. But can it be done in a way that a Stingray can’t replicate?
Thanks to [John Tirelli] for the tip!
































































































